Many books about strategy and planning focus on the income producing side of the equation rather than the operational side. Strategic Information Security.
Table of contents
- Strategic Cyber Security
- Product details
- Cyber Defence Library
- Developing an Information Security and Risk Management Strategy
For all these Internet of Things devices. Those kinds of things. Not Fitbits that you wear on your wrist, but serious things that could do serious harm like stop your heart. You want to have that information flowing in a secure way. In an encrypted, secure way. That is a solution to the problem.
Strategic Cyber Security
Now you have to make it commercially viable, which gets you into things like net neutrality. But if you were to technically solve the problem, you would begin to architect portions of the Internet. Let that be what it is. It just was too complicated. We had all these debates, all of the technical guys. We used to do this 40 years ago. It was, it was a proprietary network. We know how to do it technically. But there are people that did these things for years.
It also gives people more economic opportunity to participate. Eighty percent of the cybersecurity issues that have occurred in the commercial world are internal process and people. Or they leave it in the top drawer of their desk, and the cleaning people can go get the stuff. You would get rid of half of your problems as an enterprise if you just train your folks and put controls in place.
Did you follow the process? Password authentication and end points. If the civilian side of government,. We also talked about this idea, which never got traction in the commission report, but we thought it was a good idea where you basically would create a national ID like a credit bureau. You could create this national ID foundry where you get your birth certificate. You also get your digital identity at birth, and that digital identity is secure and protected. Now, you can modify for simple things—sharing your photos on the Internet—or you can modify it for very sophisticated things like financial transactions, your health information.
What we did was said, further studies should take place, and we recommended that Treasury would look at, further look at creating this kind of an entity. We also looked at commercial insurance as well, and the purpose of commercial insurance. Our view was that would drive up the adoption rate because people are going to want to find an insurance policy for cyber. How do you get these companies to make the investments to move up the risk-protection curve? The commission was very biased toward private-sector solutions versus government-mandated solutions. You need a private sector or an economically driven set of motivations to solve the problem.
This has been a fascinating conversation. Thank you, Sam, for taking the time to be with us today. Next up from the Forum, is Nathaniel Gleicher, who describes how businesses can learn a lot from the model of protection used by the US Secret Service. Thank you for joining us today for the McKinsey Podcast.
- Phase I—Business Awareness.
- Information security: A strategic approach.
- Annes World: A New Century of Anne of Green Gables.
- Related Video Shorts (0)?
Just make it work. The increasing scope and scale of breaches and the degree to which organizations are moving into these exposed environments has changed that. But the desire to quantify is an important change. Sometimes I think we do cybersecurity like fourth graders play soccer.
Product details
Chase the ball across the field, the whole group runs. There are always hot topics. There are a lot of tactical models, so if you look at the SANS top 20, if you look at NIST, if you look at some of these other frameworks, they will tell you, you should be investing in encryption. You should be investing in segmentation. You should be investing in certain kinds of detection.
Because of that, they have relatively few options to control that environment. Unfortunately there are no 'others' out there. Anyone considering IS security issues is faced with the challenge of managing not only the technical edifice but also the procedural and normative issues that surround the technical implementation of security measures. This book will show how this can be achieved. Increasingly, aspects of information security management are becoming critical for the survival of safe functioning of modern day organizations.
The purpose of this book is to equip managers and those training to be managers with understanding of issues related with strategic information security management. The book will also present specific tools that managers can use to address the often complex information security problems.
Cyber Defence Library
Read more Read less. Prime Book Box for Kids. Business Expert Press January 15, Language: Be the first to review this item Amazon Best Sellers Rank: Related Video Shorts 0 Upload your video. Customer reviews There are no customer reviews yet. Share your thoughts with other customers. The proliferation of cloud services and mobile devices is forcing institutions to move beyond frameworks that rely on specific technologies and to instead focus on data governance and data management issues that are technology-agnostic. The move to the cloud and users' mobile access to cloud resources also force institutions to rethink already established institutional policies.
EDUCAUSE has a number of resources that colleges and universities can consult for their information security activities, including resources on developing strategies, promoting training and awareness, and developing policies and procedures.
Developing an Information Security and Risk Management Strategy
Effective Practices and Solutions for Higher Education is the only resource developed by higher education information security practitioners for higher education information security practitioners. The guide features toolkits, case studies, best practices, and recommendations to help jump-start campus information security initiatives.
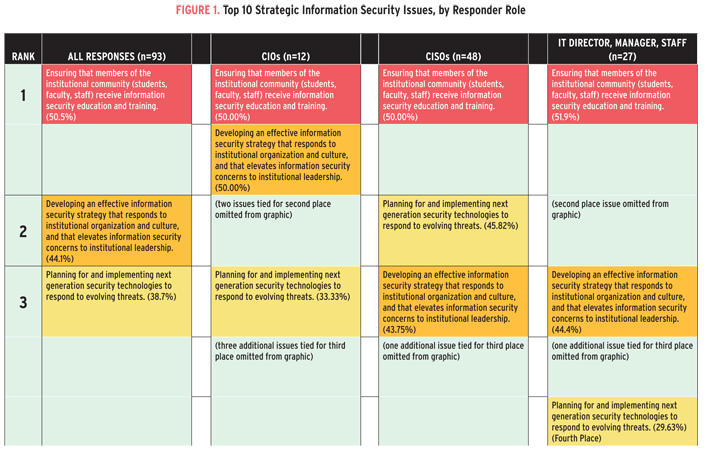
The conference showcases information security thought leadership and offers numerous professional development activities for information security professionals at all career levels. We hope these resources will be useful in helping campus information security departments successfully address the top three strategic information security issues.